42% of U.S. energy/critical infrastructure providers exposed to weaponized AI and email attacks
New research from Red Sift reveals a widespread security gap across the U.S. energy, chemical, and water and waste sectors, with 42% of 840 essential services companies still lacking effective email authentication, leaving critical infrastructure vulnerable to spoofing, phishing and ransomware attacks.
Despite rising regulatory pressure and a surge in cyber threats targeting operational technology, Red Sift’s analysis shows that nearly half of these organizations have failed to implement DMARC, the foundational email authentication standard required to block domain impersonation. Companies in the report include Chevron, Dow and American Water.
Energy sector: leading the pack. The energy sector demonstrates the strongest email security posture of the three sectors analyzed.
The report also highlights mounting regulatory pressure, including mandates under CISA guidelines and sector-specific compliance requirements. Failure to secure email systems risks not only operational continuity but also public trust and safety.
Key findings
- Chemical: 42% unprotected; 35.7% fully enforced
- Water and waste: 52% unprotected; only 23% fully enforced
- Energy: 32% unprotected; 44.5% fully enforced.
The chemical sector’s high exposure is particularly concerning given its handling of hazardous materials and complex supply chains, where a breach could have catastrophic consequences. Energy companies, 274 examined, face persistent threats from nation-state actors and cybercriminals targeting sensitive operational data. Meanwhile, water and waste firms remain the most exposed overall, with 52% unprotected.
Email-based attacks on critical infrastructure can disrupt essential services, compromise supply chains, and endanger public health. For critical infrastructure industries in the United States, DMARC is not optional, it is a cornerstone of operational security, particularly as AI continues to be weaponized by bad actors.
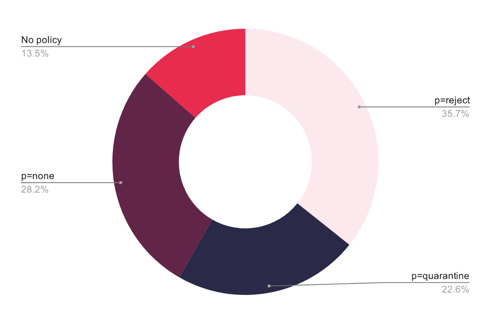
DMARC status of the U.S. Energy sector.
The takeaways:
- 274 companies examined
- Only 6% (17 companies) have no DMARC policy
- 26% (72 companies) remain in monitoring mode
- 23% (63 companies) have achieved some level of protection
- 5% have achieved full enforcement (122 at reject)
The energy sector's relatively strong performance reflects heightened awareness following high-profile attacks on critical infrastructure. However, the 32% still unprotected represents a significant vulnerability, particularly given the sector's role in national security and economic stability.






Comments